Forum Replies Created
-
AuthorPosts
-
Hi Gbatts,
AxCrypt is about strong encryption and real protection – not obfuscation. Your scenario with the compromised password is not possible to really mitigate by 2FA. As you say: “Easy peasy, decrypt the file using the same compromised password“.
That’s the thing – AxCrypt is about encryption. If the password to the encrypted data is compromised, the data is compromised as well. That’s the flip side of “If the password to the encrypted data is lost, the data is lost as well”. (There is no password reset with encryption, because the data itself is modified, it’s not about software “letting you in”).
AxCrypt is open source, and the algorithms are public and documented.
If we add 2FA, it just means the attacker will use a different implementation (or more likely, a trivially hacked version of our code) that just uses the compromised password to quietly decrypt the data.
You might feel safer with 2FA, but with AxCrypt it’s not about the feeling, it’s about the fact. The fact is:
If you lose your password, your data is lost.
If your password is compromised, your data is compromised (provided the attacker has access to the data of course).Adding 2FA to our code doesn’t change that. It is trivial to bypass.
This is the difference between encryption and access control.
If you have data protected using access control under for example Windows, an attacker can mount the disk in a Linux computer and read the data at leisure – because Linux does not implement the access control in question.
If you have data protected with strong and properly implemented encryption, it does not matter where the data is attempted to be read, or using what software. The data is encrypted, access is not determined by software – regardless of how many factors are used to allow access, in the end it’s just software saying yes or no, and this can always be bypassed by having software that always says yes.
Hi UserInterests,
It’s not about not wanting or being able to use various authenticator apps. It’s about fundamental aspects of encryption vs. authentication.
Encryption is not *access control*. When you store files in a server or a computer with access controls implemented, the software, i.e. operating system, app etc, will let you access the data if you prove that you are you. That’s authentication.
Encryption is about transforming data into another form, effectively making the content inaccessible by virtue of not being possible to interpret, under the influence of a key. A secret.
Without that secret, it’s computationally infeasible to decrypt.
That’s very different from access control, where access is controlled by software, either allowing or disallowing access. That’s where authentication comes into play – you prove to the software that you are you. But, the software can be tricked or bypassed in many different ways, because it’s only a piece of software that block or allows you access. If you’re a super-user, or can access the data without going through the software (think backup storage, remove hard drive from computer etc), you can read the data.
Encryption is not access control. Encryption is a “mathematical” transformation, requiring the knowledge of a secret to reverse. Here “2 factor authentication” or any kind of authentication, does not make sense. Because it’s not about authentication. It’s about applying an algorithm to reverse the transformation under the influence of a secret.
If we did implement an indirect scheme, were authentication (2 factor or otherwise) was used to gain access to the encryption keys (i.e. secrets), then we’d effectively be building an encryption system with a back door. That’s not what we want to do.
Hello,
See https://forum.axcrypt.net/information/license/ .
“We will always offer a no questions asked refund if requested within 30 days. Inform us via email at info@axcrypt.net should you wish a refund. Refunds are issued by reversing the initial transaction, unless we agree otherwise.”
Hi Doug,
There’s a bit of misunderstanding here.
Here’s how both AxCrypt 1 and 2 works regarding password entering requirement (although the defaults and how to change them have changed):
AxCrypt has the option of saving an entered password for re-use, so that opening many files is not a chore. In AxCrypt 1, this is not the default, but can be enabled by the “Remember this password for decryption” option. In AxCrypt 2 this is the default, but the “memory” can be set to expire after a given time of inactivity, or when a screen saver goes active, or when the computer goes to sleep etc.
AxCrypt 1 and 2 also has the option to clear the password memory, if it’s used. In AxCrypt 1 this is done through the context menu (I don’t offhand remember the exact menu text, but I think it’s something like ‘Clear Passphrase’). In AxCrypt 2 it’s done by logging out.
Once the password memory has been cleared, you need to re-enter it in order for files to be possible to decrypt, and thus view.
The crucial difference is that AxCrypt 2 does *not* have the option of *always* asking for a password, and *never* use the password memory.
What I suggest you do, is to do either or both of the following:
- Enable the Inactivity Sign Out, and set it to for example 5 minutes.
- Enable your screen saver *without* requiring a password, and set a short timeout like 5 minutes.
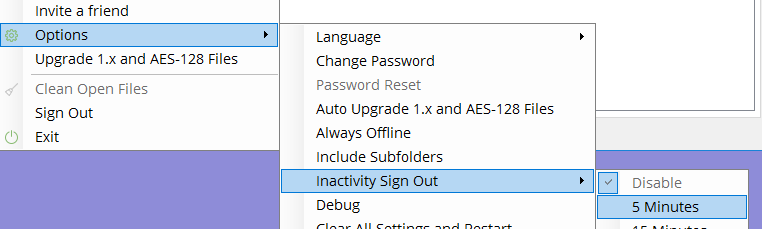
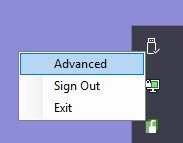
After signing in to AxCrypt (if you start it from the Start Menu) you will be presented with the AxCrypt main window, where this menu is found. If you start it indirectly, you can open it from the tray area, right-clicking and selecting ‘Advanced’:
Hello Doug!
Thanks for your input.
When I say that encryption does not make much sense if you leave it unattended without a password, I have two assumptions:
1) You use strong encryption because you *really* want to protect your data from viewing.
2) If you let anyone use your PC in your own administrator user context, they can install basically anything which includes keyloggers or other software that will make the encryption meaningless.We believe the promotion of good practices – which includes use of a password protected screen saver to avoid trivial access to the PC, in combination with usability features where you don’t have to re-type the password all the time increases the likelyhood of the solution being used, and thus protects more information.
I also believe that all you have to do is enable a screen saver – it does not have to be password protected I think, when it goes active AxCrypt should log out (I don’t have the option to test this right now, but it should work like that).
There is also an option where you can set a timeout for how long AxCrypt will open files without asking for the password again, you may want to use that.
Hello Hugh,
Thanks for your suggestions.
We do have a challenge in communicating to many users just how encryption works, as opposed to a login. In short – why you can’t perform a password reset for encrypted files, but you can do it for the login to the account.
I think you are right that we should make it clear that signing in to the account is for safety (because we then can verify that the user is using the password they think they are using without typos) and convenience (since we then use this password to actually encrypt files with).
It is *always* possible to decrypt files with the original password used at the time of encryption, regardless of the sign in password.
A new issue has been made: https://bitbucket.org/axantum/axcrypt-net/issues/454/add-link-to-new-information-page-about-how .
Hello Barry,
Please provide more information, preferably screen shots of the situation so we can determine what the situation is. The most likely reason for this error is that the file is empty (in which case it’s likely that you are using the obsolete version 1.x of AxCrypt that is unsupported) or that you have renamed a file that is not encrypted with AxCrypt to end with .axx.
But start by providing more details.
Hello Micro85,
No, AxCrypt is in no way connected to the operating system or the hardware.
One common reason for problems when moving files between computers is Windows NTFS permissions, and Windows EFS encryption – neither of which is actually related to AxCrypt in any way. If you are getting an “Access Denied” message, either of these two reasons may be the cause of the problem.
If the above does not help, please specify in more detail what the error message is.
Hello Kent!
I am sorry you’re not happy with the interface, and I appreciate you just want get your money back. No problem.
Please send an email to info@axcrypt.net and request a refund. It may take a few days for your card to be credited.
To uninstall, just, well… uninstall it as you would any Windows program (taking care to decrypt any encrypted files before you do so, otherwise you’ll have to reinstall or download the stand-alone version to decrypt the files – they are not automatically decrypted upon uninstallation).
PS – For others reading this, this is why we have a full free 30-day trial of all free and Premium features – so you can try it out in real life for a month before deciding to purchase! Do use the trial before paying anything!
-
This reply was modified 6 years, 8 months ago by
Svante.
Hi Len,
It should not have anything to do with the account.
Please make a complete error report as described here https://forum.axcrypt.net/blog/send-complete-error-report/ .
Hello Christy,
No, we don’t have a printed manual – but we do have lots of information and introductory videos at https://forum.axcrypt.net/ .
There you will find help and advice about how AxCrypt works, what it does, and what it does not. You should to start with be aware that AxCrypt is a strong file encryption software. It does not “password protect folders” as such, it encrypts files using a password as a key. There is a fundamental difference.
“Password protection” is about access control. Briefly, it means that software will determine if you have the right or access or not, based on a password for example. Windows does this when you use a password for your account for example. The thing with access control is that anyone with administrative access to the system, or direct access to the storage media using different software (for example mounting a Windows hard drive in a Linux system) can bypass access control.
“Encryption” is something else. It “scrambles” the data (in our case file by file) using a secret key to control the process. With strong encryption, the process is computationally infeasible to reverse without knowing the secret key. There is no way to bypass the encryption. Anyone can access the data – but it’s meaningless without knowing the secret key. AxCrypt uses a password to derive a secret key to use for encrypting data.
These two things are similar from a user point of view – a password is requested to access the data. But as I’ve tried to explain above, the actual process is fundamentally completely different.
Please read more at our web site, https://forum.axcrypt.net/ .
Hello Daniel,
An AxCrypt-encrypted file is just a file, nothing else. Just copy them to the USB stick and delete them appropriately from the PC after verifying that all was successfully copied, like would with any file you want to move from one media to another.
Ensuring that “no traces” remain afterwards, requires more tools than AxCrypt. While AxCrypt Premium can wipe the files so they are not recoverable by any regular utility, “no traces” requires more and may in fact be hard to achieve. So it depends on what you really mean with “no traces”.
In general, since they are encrypted, simply deleting them and emptying the wastebasket will take you a long way towards removing most traces, however for example parts of the file name may remain in the file system, and of course the encrypted data – but it’s encrypted so it’s worthless unless the password is known.
Hello Enzo,
What version and what platform are you running on?
Have you tried “Clear All Settings” – sometimes this problem is caused by windows becoming located outside of your physical screen, perhaps by having an external monitor disconnected.
Hi Leonard,
Thanks for the feedback. Some of it is are your personal opinions, they must remain so. It is meaningless to discuss the fact you don’t like the new UI design without some concrete ideas from you to improve it for example.
However, there are some technical misunderstandings that should be corrected, and some basis for changes that you may not be aware of.
“Automatic decryption” – this was always an option with AxCrypt 1.x (“Remember this key for decryption”).
“Need to be logged on” – this was also in essence an option with AxCrypt 1.x (“Remember this key for encryption”).The basic reason for making these non-optional defaults was because of usage errors of users causing data loss, as well as increased convenience. It’s simply more convenient not to need to enter your password all the time, and the “log on” metaphor is to reduce and avoid the risk of a user using different or mistyped passwords and then being unable to decrypt. This is based on real world experience of millions of users. The new model has essentially stopped data loss caused by these mistakes.
“if, by any chance, someone gets 20 seconds of access to your PC, not only you lose access to newly encrypted files, but you lose access to all your encrypted files, on all devices in sync” – This is simply incorrect. The way it’s designed you can always open the files with the password used initially to encrypt them. So you do not lose access. Also, you just can’t dismiss the fact that if you leave your PC unattended it’s not safe anymore. It’s not! You just can’t leave your PC without a screen saver or anything! If you do, it makes no sense to consider security at all.
That we changed some previously free options into paid options is of course unfortunate for you as a free user – but the alternative to getting some revenue was to simply abandon the whole thing. As it is, you can still use 1.x for as long as you like, and you get the same and in some cases better functionality for nothing with version 2.x
Thanks again for your feedback!
Hello jmh,
To our knowledge there is currently no third party software available to decrypt AxCrypt-encrypted files. However, anyone with the correct skills can create such software – the specifications are published and also the main AxCrypt software is open source.
You can always download and keep a backup copy of the standalone version of AxCrypt, or even the source code. That is all you need. You never need our servers or our company to be operating to decrypt an encrypted file.
-
AuthorPosts












