Forums › Help & support › AxCrypt Portable – truly standalone?
This topic contains 16 replies, has 2 voices, and was last updated by Hjalmar 8 years, 8 months ago.
-
AuthorPosts
-
HjalmarI have downloaded AxCrypt Portable 2.1.1494.0 to install on my work computer. I am the only person who needs to use it and I don’t need to share files.
I followed the instructions to check the cryptographic hash but my software returned a hash which wasn’t listed on that page. I presume this is because the page hasn’t been updated to reflect the most current version?
4f651672219be133716a852179a579a404e36142f71c85ca1cc9961b61a9f1a2 [SHA256]
Before I use it I have some questions. We’re not allowed to use anything that changes the context menu or makes registry entries. Also the computer I’m using it on does not have a network connection which is why I downloaded Portable.
- Can Portable be used in the always offline mode?
- Does it ever need an internet connection?
- Does it make any registry entries?
- Apart from the encrypted files does it leave any other files (e.g. settings. key pairs) anywhere on the computer?
- If I delete “AxCrypt-2.1.1494.0.exe” will that be everything gone?
Thankyou.
Picture of the website I downloaded it from.

HjalmarAnybody, please? Could you confirm if it’s the correct file?


ThorThe signature chain looks okay to me (and the hash sum is the same one that I got when I downloaded it) but I don’t use the portable version so I can’t answer your other questions, sorry.
The SHA-512 is:
752f3e2e381e6d4f8495ca49e37110d9727a3a914ad81b1224ff77e4e55123b52beaaa497935840d09ae89bc7cd01c28d2d1f46595c60eff040160a4d606e640
Checking the hash sum and the Microsoft Digicode is best practice to be absolutely certain that the software is authentic. The former (the cryptographic has) is more reliable than the latter (Digicode) but it’s less user friendly.
The file is listed okay on the famous virustotal website.
Hello Hjalmar,
The signature and the hash is correct. We’ve now updated the list of hashes to include the new version as well. Sorry about that.
The portable version stores temporary and configuration files in %localappdata%\AxCrypt but that’s all. If you run in it in ‘always offline’ it will always be offline.
It does not ever need Internet if you run in it ‘always offline’, and does not store anything in the registry.
HjalmarAwesome.
Thankyou Thor and Svante for your rapid replies.
I can use the software now that I know it’ll leave minimal data. 😊
We have a strict computing policy at work and this will be okay.
Hjalmar,
If you want to be really sure – download the source and compile it locally, then you can inspect every line of code to ensure it does exactly what it should.
Hjalmar,
If you want to be really sure – download the source and compile it locally, then you can inspect every line of code to ensure it does exactly what it should.
HjalmarI’ve compiled the software now and it works I’m pleased to report.
I noticed one thing that I would bring to your notice. I was looking at the difference between Premium and Free and I saw a global variable which AxCrypt uses to determine a users’ status. It’s not difficult for somebody to “play the system”.
With open source software enforceable licensing is always going to be an issue and you may say that people could remove the relevant licensing from the source code but I didn’t know if this was an oversight on your part?
I’ve been deliberately vague and please feel free to delete this message. I agree that the implementation doesn’t impinge upon the security of AxCrypt but a bad person might deprive you of revenue by cheating. 😞
HjalmarI am going to review the source more thoroughly but I am happy to see the Bouncy Castle is being used. If I see anything wrong I will draw it to your attention in an email. 👍
HjalmarI’ve had a look at the software and it’s very good. There’s quite a bit of redundant/old code but I know this is a natural part of software development.
I’ve noticed a few issues on inspection and I’m going to review everything when I have chance. I’d like to tell you of some things I came across. Sorry if these are already known to you; I’ve not looked through your full list on BitBucket.
Notepad Issue
1 – Create a file in Notepad
2 – Save the file as ‘Test.txt’ and quit notepad
3 – Drag into ‘Recent Files’
4 – Double click ‘Test.txt’ in ‘Recent Files’ to open
5 – File opens and red broom appears
6 – Close ‘Test.txt’ and file closes and red broom disappears7 – Repeat process above but;
8 – Open a new instance of Notepad (at any time prior to step 6 above) and leave it open
9 – Close ‘Test.txt’ and file closes but red broom remains
10 – Close new instance of Notepad and red broom disappearsPaint Issue
1 – Create a file in Paint [pbrush.exe]
2 – Save it as ‘Test.png’ and quite paint
3 – Drag into ‘Recent Files’
4 – Double click ‘Test.png’ in ‘Recent Files’ to open
5 – File opens in ‘Photos’ [Windows 10] and red broom appears
6 – Close ‘Test.png’ and file closes but red broom remains
7 – You have to manually click the red broom to erase temporary dataReport Snapshot
1 – Reproducible when invoked with -offline switch
2 – Reproducible when ‘Always Offline’ set
3 – If file deleted it is recreated upon next program full reload
4 – If file is not deleted, no further entries are made
5 – Is AxCrypt trying to connect to service despite user setting offline option?
6 – Example below (date and time removed):Axantum.AxCrypt.Common.OfflineApiException: Internet Unavailable GET https://account.axcrypt.net/api/global/apiversion
at Axantum.AxCrypt.Mono.RestCaller.<SendAsync>d__1.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.CompilerServices.TaskAwaiter.ThrowForNonSuccess(Task task)
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Axantum.AxCrypt.Api.ApiCaller.<RestAsync>d__1.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.CompilerServices.TaskAwaiter.ThrowForNonSuccess(Task task)
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Axantum.AxCrypt.Api.GlobalApiClient.<ApiVersionAsync>d__12.MoveNext()Suggestions
1 – Add ‘Open With’ context menu in AxCrypt UX (upon right click) to allow file to be opened with non-default application
2 – Add ‘Anonymous Rename’ in AxCrypt UX (upon right click) as it’s quicker than using the ‘File’ menu
3 – You have to open file (once you’ve dragged it back into ‘Recent Files’) before AxCrypt will show the name of an Anonymously Renamed file
4 – Allow password change offline. Maybe only for ‘Always Offline’ users because of potential sync problems otherwise for Premium users where key files need to be uploaded to your servers
5 – ‘Export AxCrypt ID Secret and Sharing Key Pair’ encrypts that file with AxCrypt. Whilst the ‘Import AxCrypt ID with sharing and access keys’ is greyed out it’s non-intuitive to users (especially as the exported file doesn’t appear in ‘Recent Files’) that the file needs decrypting prior to use: unless when you activate this feature AxCrypt decrypts the file
6 – Is it necessary to encrypt the private key? The private key is unusable without the password. It’s a nice added level of security provided that this is explained to the user
7 – A lightbulb is non-intuitive for a ‘Check for updates’ option. Consider having an exclamation mark or another more representative icon. A lightbulb looks like a ‘Tip of the day’ that people will ignore
8 – “Your version is old. Please click to check for a newer version” lightbulb appears when in offline mode. Consider allowing the user to remove it via a menu option. They shouldn’t have to add a “LastUpdateCheckUtc” or “NewestKnownVersion” entry
9 – Re-order ‘Help’ menu so that ‘About’ is at the bottom – i.e. ‘View Help’, ‘Check for Update’, ‘About’
10 – Consider changing the ‘Password Reset’ name to ‘Destroy AxCrypt Account’ to make it clear to users that a password reset won’t give them access to their files; it’ll destroy their account and allow them to start afresh
11 – If a user activates debugging it appears to send information to the server by default. If this is so, consider having a ‘Send Debug Logs’ option instead
12 – Debug has ‘Check Version Now’ in addition to the ‘Help’ menu
13 – Have a warning upon clicking ‘Clear All Settings and Exit’. This can be done by mistake at the moment
14 – Upon first start consider re-phrasing “a real email address is required” or put a note in smaller text saying explicilty that they can enter a fake one. It also says “Click help for more information”. They can’t; it’s greyed out. Perhaps re-phrase to “Click the question mark for more information” or add a ‘Help’ button
15 – Upon first start allow the user to bypass the AxCrypt ID email address entry to allow them to import previous keys. The only way at the minute would be to manually copy the configuration files into the correct directory. Having an option to bypass the screen would also allow them to decrypt files without entering any detailsBugs
1 – Using Anonymous Rename causes file to disappear from ‘Recent Files’
2 – Secured Folders take a while to recognise/encrypt new files. The red broom (or quitting AxCrypt) forces the files to be encrypted immediately3 – ‘Stop Securing’ feature doesn’t work properly in a Secured Folder. It will decrypt the file but as soon as the program is quit, or the red broom is clicked, the file will be encrypted again
4 – ‘Create AxCrypt ID’ is always greyed out. The only way to do this is delete the configuration files or by ‘Clear All Settings and Exit’Dialogue Suggestions
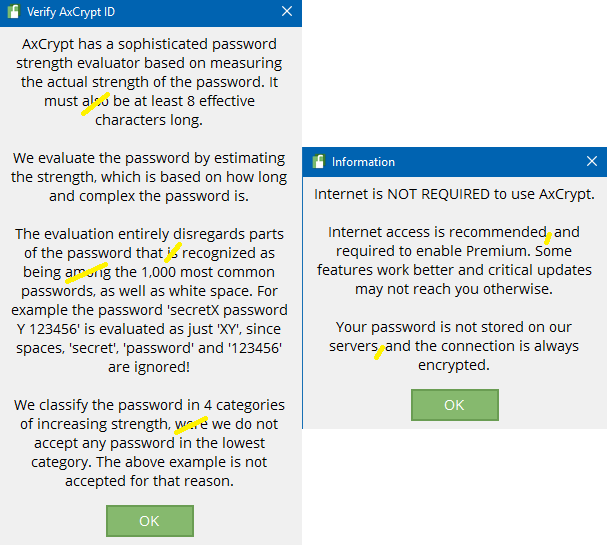
1 – Maybe remove the word “also” from first paragraph
2 – “that it recognises” or “that are recognised” but not “that is recognized”
3 – “amongst” not “among”
4 – Last paragraph “where” not “were”
5 – Remove superfluous commas
These are only very minor corrections to make the interface clearer.
I also had a think about the licensing and it’d be very difficult to implement anything effective (even like PKI) because it could easily be removed. At least any bed people wouldn’t have access to the key sharing functionality (because that requires your servers) or the mobile apps (same reason). It also inconveniences them because they’d have to use the software offline most of the time. So perhaps it’s just right as it is.
HjalmarI think the Notepad and Paint issues are because of threading in Windows and not something AxCrypt can do much about without putting data at risk.
It’d be nice for an ASCII armour format for encrypted data because any small change to a .AXX file causes the whole file to be unrecognisable. At least with ASCII armour it’s easy for people to export as plaintext.
Hello Hjalmar,
What can I say? Thanks! Lots of very good and relevant thoughts and notes. Some are on our issue list, some will soon be ;-)
One thing surprised me – you say there’s lots of dead and unused code? Could you point me in the general direction, I try very hard to get rid of dead code as soon as it’s dead. One thing you may not be aware of is that while the Windows desktop and the core libraries are open source, we also use the core libraries in our mobile apps, our soon to be released Mac app as well as on the server side ( https://account.axcrypt.net/ ). So, if the methods are public, they may be used by other code that is not part of the axcrypt-net repository.
The plan is to separate the core libraries into a published SDK nuget package once the most intense development phase is over. But for now, when we have no less than 5 platforms rapidly moving forward using the core libraries, it’s just so much more convenient to include it as a source dependency.
Also, about the ease of cheating with the Premium status, it’s a known situation and conscious decision although we will do a few minor changes in the near future where it at least requires you to hack the source. It’s hard to make strong DRM with open source like this. In the end there will always be a place in the code where the policy is applied, and where someone can hack it away. With or without the source, but it’s of course so much easier with the source. We could obfuscate and do sneaky things, but it just doesn’t make sense for us. If someone really wants to hack the source to get at the Premium features – so be it. There’s still quite a bit of things that are outside of this, which includes the mobile apps and the server-based features (of course if you want to be always offline, none of that makes much sense to use anyway). I could even consider making Premium the default in always offline mode!
As for always offline causing an OfflineApiException I seem to recall that’s just how it’s implemented. Normally, if a connection to the server fails, we throw an OfflineApiException. If we’re always offline, we do the same but before even trying, causing the rest of the code to see no difference between “unplugged”, “server down” and “always offline”.
In any case, the level of your comments indicates I’d like to talk to you. Please PM me via support att axcrypt dott net if you will. I gather you and your employer values privacy to a great degree, and I’ll be happy to respect that of course.
HjalmarIn any case, the level of your comments indicates I’d like to talk to you.
I have replied via email. 🙂
HjalmarI have two more suggestions:
- When creating a new account via the software it prompt for a password. It uses a basic algorithm to detect weak passwords but it allows you to use your email address as your password!
- The encryption password is transmitted via TLS. There are a number of solutions for this but they’re complicated and involve extensive development effort. However if I’ve understood the technical documentation correctly, there seems to be one simple fix which I’ll explain below.
A file encrypted with AxCrypt (AXX) is highly secure by today’s standards. If the AxCrypt binary contained a hard-coded AxCrypt public key (the EXE is secured with Authenticode and a verifiable cryptographic hash) then upon the user entering their password it could be encrypted into a miniature AXX file, transmitted to the server via TLS, decrypted with the AxCrypt private key on the server and then validated. There’d be an insignificant increase in time but the security would increase tremendously.
Some may argue that TLS is fundamentally compromised. Whichever side of the fence you’re on – by double encrypting the password (i.e. transmitted over TLS and encrypted with the AxCrypt public key) it’d minimise any risk of compromise by TLS, e.g. fake root certificate installed on the local computer, antivirus, ISP etc. – see my email for other methods.
Of course this wouldn’t prevent capture from key-loggers but it’d remove several side channel attacks against the password. It’d also satisfy many who don’t trust TLS. They’d still have to trust the server but it’d be an enormous increase in security.
It may not be practical depending upon the server configuration but it’s a relatively easy way to increase security without requiring a significant amount of development or even server resources.
Hello Hjalmar,
Thanks again for your input. Yes, the SSL/TLS issue is frequently debated and many distrust it for the reasons you describe, and with reference to various conspiracy theories.
I like your idea of using AxCrypt to encrypt the password as it is sent to the server, we’re actively trying to make the analysis as simple as possible, and that entails using / relying on as few mechanisms as possible. We’ve already discussed various ways of strengthening the protocol, including making a zero knowledge variant. (The problem with that is that some other things become less convenient. But that’s a longer discussion.)
The problem that will have to be investigated is just how robust such a large HTTP header is in practice. For it to be a relatively “simple” fit, I’d like to continue using basic authentication, and this entails sending the password in a HTTP header. A minimum AxCrypt file right now weighs in at about 5K, this can probably be reduced a little by extending AxCrypt to support a file-less format (that’s useful for other situations as well, such as AxCrypt-encrypting pure text etc), thus reducing the amount of headers etc, and perhaps even skipping the redundant headers in the trailer. But then it has to be Base-64 encoded, so it grows again. In the end the header will probably be on the order of 4K. To be honest, I just don’t know how will this will work. A mitigating factor is that it’s still inside a SSL/TLS connection so it should not be affected by intermediate stuff.
Still, I like it. Even better, it can be added without any problem for existing clients. The server can easily distinguish between the cases.
See:
https://bitbucket.org/axantum/axcrypt-net/issues/276/filter-out-components-from-the-user-email
https://bitbucket.org/axantum/axcrypt-net/issues/277/implement-file-less-axcrypt-encryption
https://bitbucket.org/axantum/axcrypt-net/issues/278/investigate-and-possibly-implement-axcrypt
Thanks!
-
AuthorPosts

