This topic contains 134 replies, has 3 voices, and was last updated by Doug 6 years, 6 months ago.
-
AuthorPosts
-
Hello Mari,
Thank you for your input. We’d love to please everyone, but as it stands we simply don’t have the resources to work on version 1 as well. The source is out there, but apparently although over 20 million people have tried and used AxCrypt 1, not a single one of them have felt that it’s worth the time and effort to continue working on version 1 either… The source code is out there, so anyone with the right skills certainly could do it!
Right now, I can’t suggest a replacement – but we are working on making the AxCrypt 2 experience being improved as we go along.
For what it’s worth – we’ve received many comments to the effect of “I was initially disappointed like so many others by version 2, but after using it a while I realize that the changes are actually an improvement”.
So, you might also want to give it a try…
Hello Zulu,
Thanks for your input!
I’ll try to respond to some of your concerns.
“Why does it need to go online at all?!” – It doesn’t, you can use it entirely offline. Online does offer some advantages though.
“Why do you need a verified email address for the user?” – Two reasons: One as you say to support the business model. But the other reason is because it enables us to communicate with users, and it helps us immensely when we provide support. Although we log very little, and no individual encryption / decryption actions, we do log events such as failed and successful sign ins, password resets (the fact, not the password) etc. This gives us a chance to help users who have gotten themselves into trouble.
“… the comments/reviews the downsides of AC2 are pretty much related to a business model need rather than a user functional need” – Some few changes are indeed to support the business model, but they also overlap with features and user friendliness aspects. The account email is for example also used to implement the key sharing functionality, which has been requested by many for a long time. This enables us to use a single password model for all AxCrypt functions, while allowing you to share encrypted files securely with others using advanced public key technology without hardly noticing it. This also enables a feature even if you don’t share with anyone – if you change your password, this new password can be used to open even old encrypted files, since we always ‘key share’ encrypted files with yourself.
“It does not need much functional change from year to year ( 95% of its function was present in version 1)” – Not really true, and with version 2 we now support iOS, Android and OS X, also requested by many for many years.
“Rather charge a nominal fee for version 1.8 which would include 256 encryption than pursue AC2 would be my recommendation” – We have of course considered this, but there are some problems. It’s a non-trivial thing to implement, and we just don’t think it’s worth the effort. But, the source code is out there, so anyone could if they wanted to! I’d be happy to give advice and some support to a serious such effort.
“The new website for AC2 lists and uses links for reviews of AC1 as support for a reason to buy AC2” – We feel this is fair, because effectively, version 2 is a superset of version 1. Even the normal use case is click and type identical! If you close your eyes and don’t look at the different look, the clicks and typing is actually identical to version 1 with “Remember this password for encryption and decryption” enabled.
And, as you’ve noticed, we do keep the old version around and will continue to do so indefinitely.
Vagner DantasI agree with users say that the 1x version is much easier than 2x. Maybe for free users the 2x could have a menu or a setting equal to the 1x.
Jag håller med med användare säger att 1x-versionen är mycket enklare än 2x. Kanske för gratis användare kan 2x ha en meny eller en inställning som är lika med 1x.
billi left AxCrypt for similar reasons, besides paying every year (i hate subscriptions), the online account adds complexity and an internet requirement.
Hello bill,
Sorry to hear it! What were you paying for the old version 1 if I may ask ;-) ? You do know that essentially equivalent functionality is still free in version 2? Unfortunately we have bills to pay every year, and with a regular license model we either have to keep finding new paying users at a steadily increasing rate (if we want to grow and improve the software), or engage in the continuous version-switching and upgrade “offers”. AxCrypt 1 stayed at version ‘1’ for 15+ years. Version ‘2’ has stayed at version ‘2’ for 4+ years. With a license model we’d be forced to bump the major version every year or so in order to entice or force you to upgrade… We really do think the subscription model is a more honest way of doing business.
The online account has its’ sides, some plus and some minus. We think benefits far outweighs the disadvantages. You can of course run AxCrypt 2 entirely offline if you insist. Just enable the ‘always offline’ option. You still have to do a ‘registration’, i.e. assign a user name, but the information is never sent anywhere. All is 100% local.
elwin chowdont like axcrypt 2.. because 1 password to all files.. I scare if someone can acces my computer then he can acces all my encrpyt files…
how if every want open some files, we need typy password no just open like now.. maybe it more safe
Hello elwin,
One strong password is actually safer than many not-so-strong passwords, and just as safe as many strong passwords.
No, having access to your computer does not typically mean they have access to your encrypted files. However, if someone does have access to your computer, you can in principle no longer trust that computer for anything since any kind of software may have been installed by the person gaining access. The good thing about AxCrypt is just that – gaining access to the computer will not (at least in the first stage) gain access to encrypted files.
zulu53Svante is correct in his comments: however you are correct in your fear of version 2. The real issue is that Svante changed his business model from v1.7 to 2 and showed that he was tying is individual (and immediate family) financial and personal security to Axcrypt. He will be the one that has installed the “backdoor” and his server based “password collection” system in version 2 and will under promise of reward (money and financial security) or penalty (physical threat to his family – going to jail) give your passwords to anyone how asks and rewards or penalizes him. I only use a copy of v1.7 that I downloaded many years before he changed his model (and was relatively unknown to codebreakers). I don’t use the current copy of v1.7 put on the old website since it may have been compromised when the business model was changed. If Svante wanted to give some confidence in his claims of security he would make 1.7 open source so it could be at least checked for backdoors”.
markI continue to receive error messages for files in only one folder on my tablet. I believe I used Microsoft encryption for these files prior to my upgrade from AxCrypt 1.7 to 2.0, and now these files are “double encrypted” which is preventing me from decrypting these files with the new version of AxCrypt. Microsoft is precenting me from changing the attributes of these files. Do I need to uninstall AxCrypt version 2.0 and reinstall version 1.7 in order to decrypt these files, then change the file properties (undo the Microsoft encryption), and then reinstall AxCrypt version 2.0? What will happen to all my other files (which have no issues with access) while I transition between the two versions of AxCrypt?
Hello mark,
AxCrypt 1.x and 2.x are compatible in the sense that 2.x can open all files secured with 1.x. In addition to that, 2.x implements of lot of new rich features, while some functions of 1.x are deprecated. Files secured with AxCrypt 2.x are not possible to open with AxCrypt 1.x.
Please note: You cannot have both AxCrypt 1.x and 2.x installed at the same time.
Still, you can open/decrypt the old encrypted files with the original file password(which was used in the file encryption process).
If the above does not help,please provide more information about the issue and write a mail to support@axcrypt.net . you can send a screenshot showing where the problem is, it often helps us understand.
DougI only use the free version(s). Version 1 was simple and easy to use. Version 2 is simpler, and yet your logic for one being able to walk up to my pc and open an encrypted file is incorrect.
You say that if anyone can walk up to my pc and use it without a pc/Windows password, it isn’t safe anyway. But I don’t use file encryption to make my pc safe. I use it to make individual files or folders of files safe. If a pc/Windows password keeps people out, why would anyone need encryption for a file? Microsoft has continually opted to make it possible for people to use Windows without a pc/Windows password. Why? Because not everyone needs them…risk vs. convenience. But those who do not need a pc/Windows password may very well sometimes need to encrypt something to keep prying eyes out.
Think of it this way. A person’s pc may be left on at times, because personal pc’s are at home, where typically there is no one around to physically access the pc. If a hacker makes it on board and takes the time to crack my encrypted files, then he/she gets to view them. I’m not trying to be Fort Knox. I’m trying to simply make it so that in the event someone, even another family member from across town for instance, walks in, sees my pc…and perhaps it is up and running Windows…and they sit down to use it. I have no problem with them using my pc…but I do have a problem with them viewing certain files. For some files, there is a legality issue to have the files available to read. A hacker could care less about the information in these files, for he/she cannot use them to make money. But it is important for them to be difficult to view. With version 2, it isn’t just a matter of personal choice…using version 2 is basically like using nothing. I mean…just who, at what point, is protected by an encrypted file that anyone can view once the pc is accessed? Basically no one in my opinion.
Are you actually suggesting that people with good pc passwords never get hacked? Not so! The Internet provides a ready passage for a good hacker.
So okay, you’ve decided to do it this way…and to let the old way that so many people loved slip away into history. I think there should be an option to allow users for whom the old system worked better (procedurally) to use version 2 in the same way they used version 1. The sign-in could be an additional layer of protection (optoinally a 2nd requirement in addition to the encryption password), rather than replacing the password prompt. Or…if such an arrangement wasn’t needed, version 2 could be used the way it is currently designed/configured.
As for me, you’ve made the program 100% useless to me. I don’t see how that is progress…unless one or more optional procedures for use are constructed and made available. Hey…I have to rethink my decided course of action sometimes too.
Doug
Hello Doug!
Thanks for your input.
When I say that encryption does not make much sense if you leave it unattended without a password, I have two assumptions:
1) You use strong encryption because you *really* want to protect your data from viewing.
2) If you let anyone use your PC in your own administrator user context, they can install basically anything which includes keyloggers or other software that will make the encryption meaningless.We believe the promotion of good practices – which includes use of a password protected screen saver to avoid trivial access to the PC, in combination with usability features where you don’t have to re-type the password all the time increases the likelyhood of the solution being used, and thus protects more information.
I also believe that all you have to do is enable a screen saver – it does not have to be password protected I think, when it goes active AxCrypt should log out (I don’t have the option to test this right now, but it should work like that).
There is also an option where you can set a timeout for how long AxCrypt will open files without asking for the password again, you may want to use that.
DougHi Svante,
Thanks for your response.
If I were to use a pc/Windows password (which I won’t), the issue of always typing a password arises whether AxCrypt asks for one or not…and does so for all file viewing or use.
The preventive feature you speak of regarding a screen saver is a feature I cannot see or adjust. I could use a simple screen saver, but AxCrypt-ed files would be available the instant it vanished and would not then require a password.
The feature re screen saver you mention which will periodically require a password is a work-around approach, and does not keep someone from viewing the file. Also, I do not see a way to use that feature. AxCrypt runs in the background, and there is no program with settings available to adjust. I click AxCrypt in my Start Menu and short of a brief hourglass, nothing pops up or becomes visible (Windows 7 on this particular pc, native Windows 10 on the other).
Sorry, Svante, I just don’t see how your chosen logic plays out in a way that has AxCrypt 2 actually protecting files from being viewed. Version 1 worked great!
Due to a hardware failure, it became temporarily necessary to use this Windows 7 pc. In setting it up with my files, I noticed a group of files that should have been protected but weren’t. So I dutifully set about to remedy that problem…by installing AxCrypt (version 1 install file I already had). Unfortunately, as you know, it no longer protected from viewing. Research on your site revealed that it is obsolete and that you recommend against its use. Okay…great…I see you have a new version (2) with a free version still available. I uninstalled, rebooted and downloaded/installed version 2. I’m glad I was using the free version because using it brought me to the realization that AxCrypt no longer prevents viewing of a file. Again, I ask you: What’s the point of a file encryption that doesn’t protect a file from viewing? If the features you mention were setup and in use, someone could still view these files quickly, one at a time, and apparently make screen shots of sensitive data (manually or with an automated fast frame capture utility available free on the web).
Your response is very polite, and reiterates your point of view as being the “more secure” way of doing things. However, it completely misses and avoids the obvious fact that AxCrypt 2 does not protect files from snooping. It doesn’t do anything useful (to me) at all! The only visible differences in a file using AxCrypt 2 is an added filename extension and a new green icon indicating AxCrypt is in use. But in use doing what useful function? Nothing.
You spin a good yarn about security, etc., but you didn’t/don’t address the key issue: Why would anyone, anywhere, with any situation, with any type computer or other device, encrypt any file???
Well, they do it for one reason (in a variety of forms): I/they want to prevent viewing of that file!!! Period!!!
If someone uses my computer and can read the encrypted files present, regardless of how secure the pc is or the situation, then they can read the files I don’t want them to read…that I am not allowed to let them read.
On the other hand, if I were to use a pc/Windows password as suggested (and there have been situational instances when I did establish such a password, then removed it when no longer needed)…why would I need to encrypt any files at all? By your logic, the pc/Windows password will prevent people from viewing the encrypted files, and basically all files. If someone is thus prevented, I would never need a file encryption software. But…if I did still use AxCrypt on certain files, once in they could still view these files.
So you really, really need to ask yourself: What’s the real point of AxCrypt? In either case, it no longer protects files.
Doug
Hi Doug,
There’s a bit of misunderstanding here.
Here’s how both AxCrypt 1 and 2 works regarding password entering requirement (although the defaults and how to change them have changed):
AxCrypt has the option of saving an entered password for re-use, so that opening many files is not a chore. In AxCrypt 1, this is not the default, but can be enabled by the “Remember this password for decryption” option. In AxCrypt 2 this is the default, but the “memory” can be set to expire after a given time of inactivity, or when a screen saver goes active, or when the computer goes to sleep etc.
AxCrypt 1 and 2 also has the option to clear the password memory, if it’s used. In AxCrypt 1 this is done through the context menu (I don’t offhand remember the exact menu text, but I think it’s something like ‘Clear Passphrase’). In AxCrypt 2 it’s done by logging out.
Once the password memory has been cleared, you need to re-enter it in order for files to be possible to decrypt, and thus view.
The crucial difference is that AxCrypt 2 does *not* have the option of *always* asking for a password, and *never* use the password memory.
What I suggest you do, is to do either or both of the following:
- Enable the Inactivity Sign Out, and set it to for example 5 minutes.
- Enable your screen saver *without* requiring a password, and set a short timeout like 5 minutes.
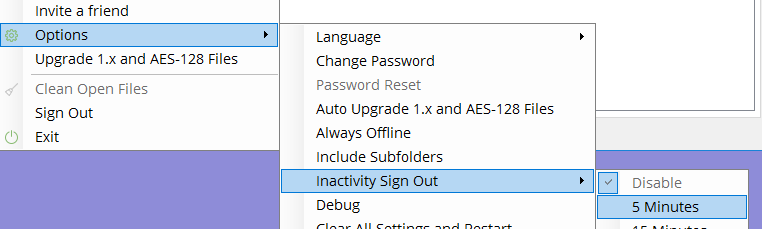
After signing in to AxCrypt (if you start it from the Start Menu) you will be presented with the AxCrypt main window, where this menu is found. If you start it indirectly, you can open it from the tray area, right-clicking and selecting ‘Advanced’:
DougI see now that the main window can be accessed via the Taskbar. Unfortunately, the feature you mention is unavailable in the Free version. Inactivity Signout is set to disabled (checked) with that setting and all settings for that selection. It is, along with most all selections, an upsell to the Premium plan. I’ll check back for your reply, but apparently I’ll have to uninstall and move on.
-
AuthorPosts

